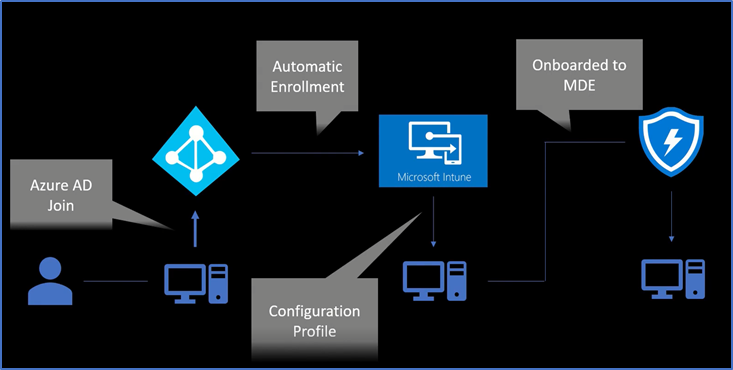
It is a hot topic these days to onboard Windows devices to Intune and Microsoft 365 Defender ATP. And in this blog, you will learn to onboard Windows devices to Microsoft Intune and from there to Microsoft 365 Defender.
Now in this case what will happen a device object will get created in Azure as well and from there the device gets onboarded to Microsoft in tune because we have enabled automatic enrollment and then there is a configuration policy that exists in Microsoft Intune which will get the device onboarded to Microsoft defender.
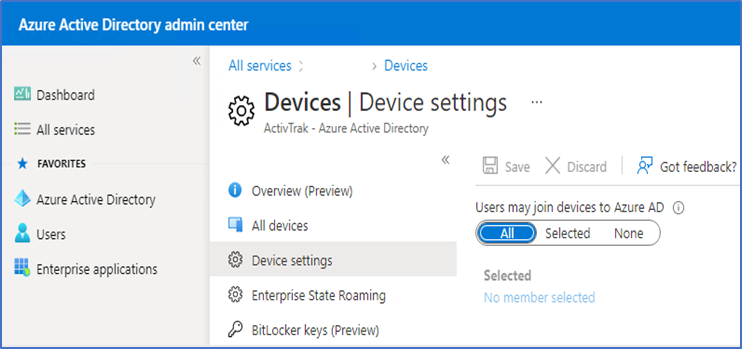
Now for that you have to go to Azure portal, Azure Active Directory > Devices > Device settings and check if the setting is enabled for all users.
Then go to Mobility (MDM and MAM) > Microsoft Intune on Azure portal.
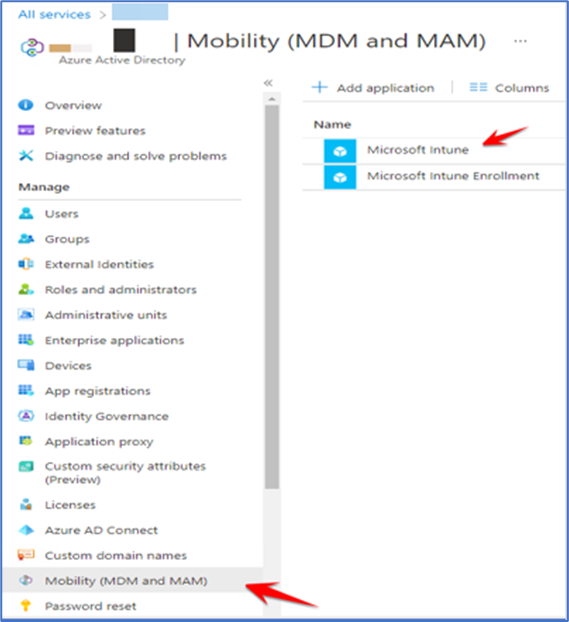
If I go to this particular section which says “Mobility (MDM and MAM)” and here what I have done is I have scoped Microsoft Intune for all users or for all the categories to be very precise.
This scope is for when the device will get onboarded to Azure active directory, so set the scope either for all users or for specific groups.
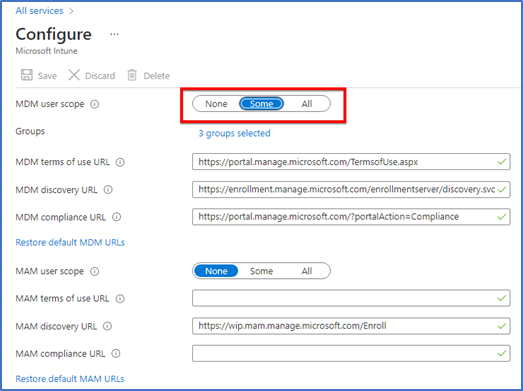
When the above settings are enabled, you can verify that from Intune portal “Endpoint.microsoft.com” also.
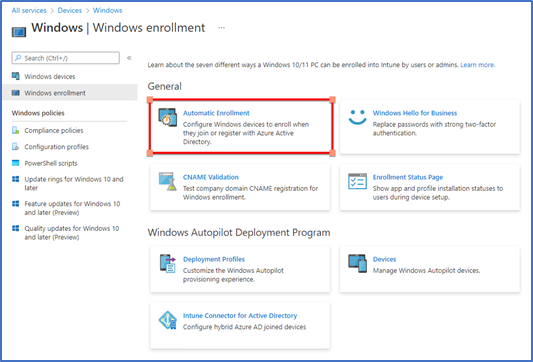
Devices > Windows > Windows Enrollment > Automatic Enrollment
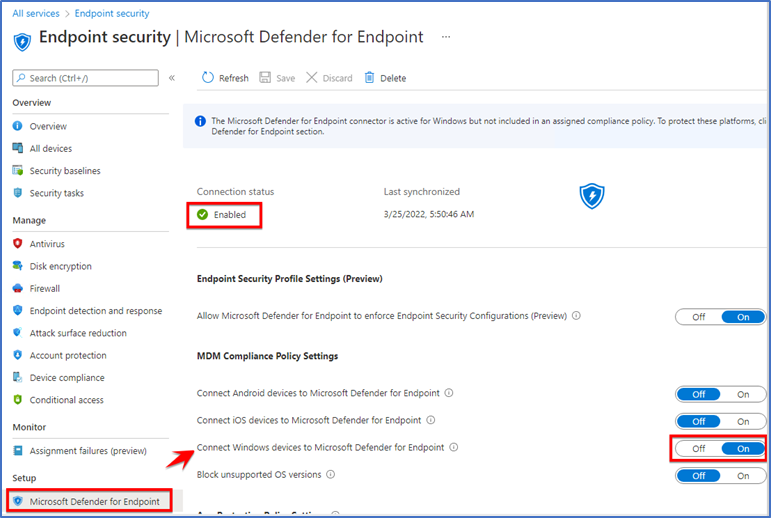
On Intune portal you have to go to “Endpoint security” section and here just click on “Microsoft defender for endpoints” just enable this particular connector it is required. Second thing you have to make sure that this particular option is enabled which says “Connect Windows devices to Microsoft defender for endpoint” because currently we are onboarding Windows device.
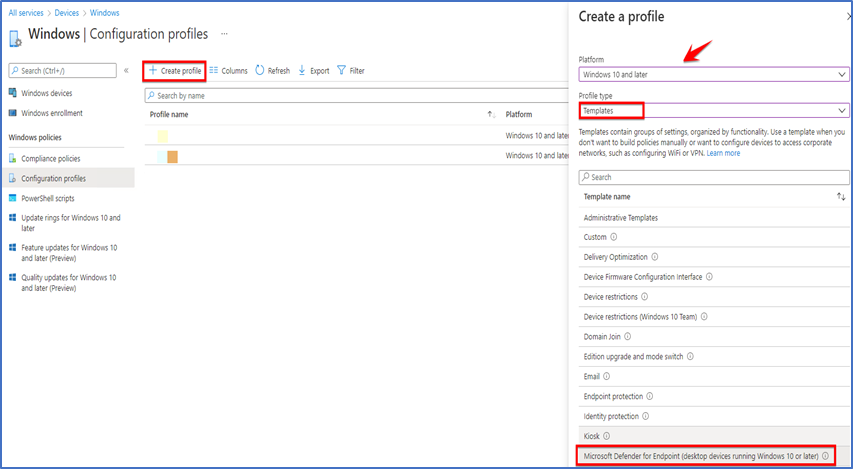
Then Go to Devices > Windows > Configuration profile and then click on “Create profile” from here select “Windows 10 and later” and then select “Templates” you will get this option which is “Microsoft defender for Endpoint(Desktop devices running windows 10 or later)”
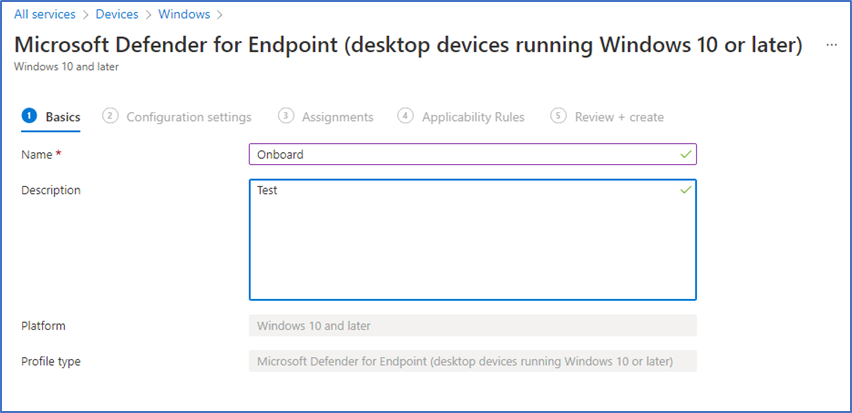
Name the profile, I just named it as Onboard and in description as Test. You can give the name and description according to your requirement.
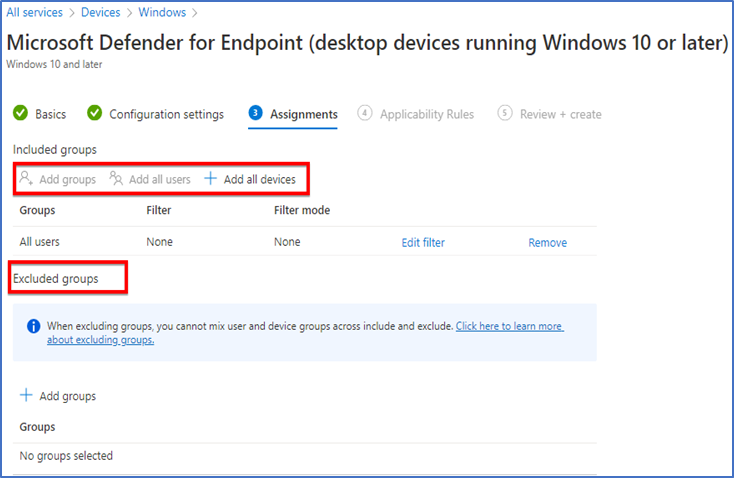
When I come to ‘’Assignments’’ you can scope this polices to specific ‘’groups’’ ‘’devices’’ or ‘’ Users’’, whatever scope you required.
For “Applicability Rules” you can create a rule as per your requirement or you can also leave this section if not required.
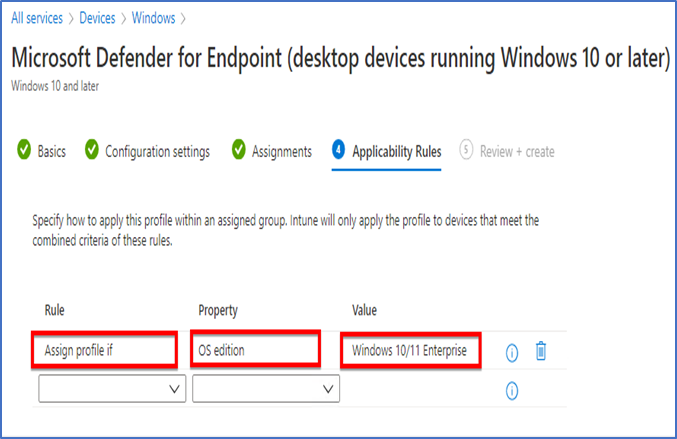
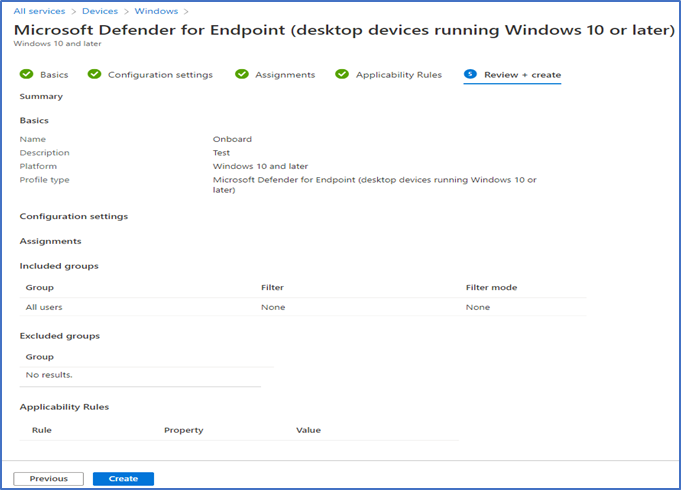
Review the settings and click on create.
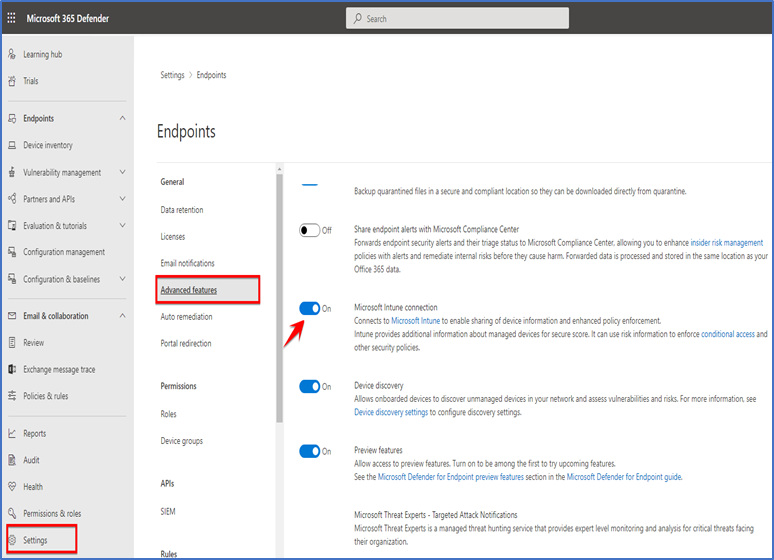
Go to Microsoft 365 defender portal “Security.microsoft.com” Settings > Advance features and enable Microsoft Intune connection.
Then go to your Windows device and open account settings. You’ll find an option to connect, click on that then select join this device to azure active directory and enter your Microsoft Ad account and hit next button. If you are installing new OS then you’ll find an option there to join this device to Azure AD, enter your Microsoft Ad account there and device will automatically register to Azure AD.
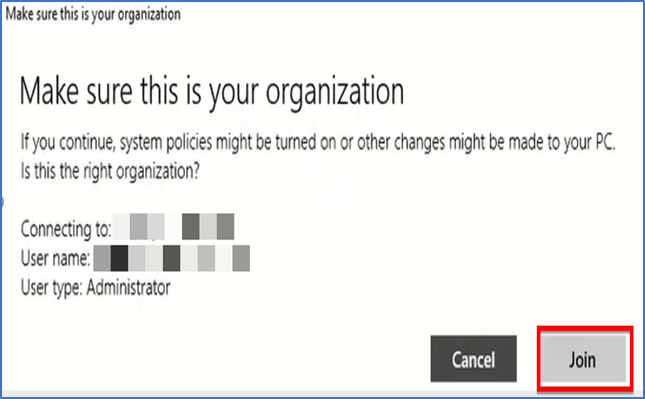
Confirm it is your organization and join.
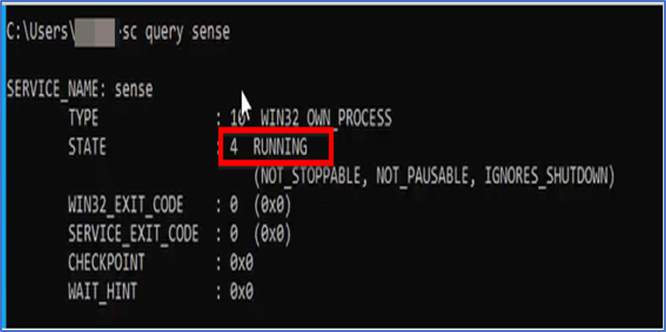
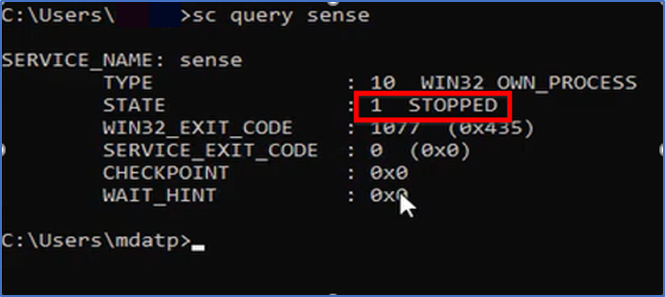
Check if Microsoft Defender is running on your system, you need to open CMD and run “sc query sense” command. If it says “Stopped” then device still taking time to onboard and you have to give it sometime then reboot it.
Type same command again and you will see it says “running” which means device onboarded successfully and you can also confirm from Microsoft defender portal > Device Inventory.