Device compliance policy helps to protect organizational data by requiring users and devices to meet some requirement. It only checks if the certain settings are enabled or not. In this article we will create compliance policy for our Windows device. If you have issues onboarding your device then you can take a look on my other articles in which I have wrote in detail regarding onboarding via Auto Enrollment and Autopilot deployement. Below are the links for those articles.
1. Automatic Enrollment of Windows 10 devices on Microsoft Intune: https://lnkd.in/dNPwsz7w
2. Onboard devices to Intune via Windows Autopilot Deployment Program: https://lnkd.in/dSdcgYms
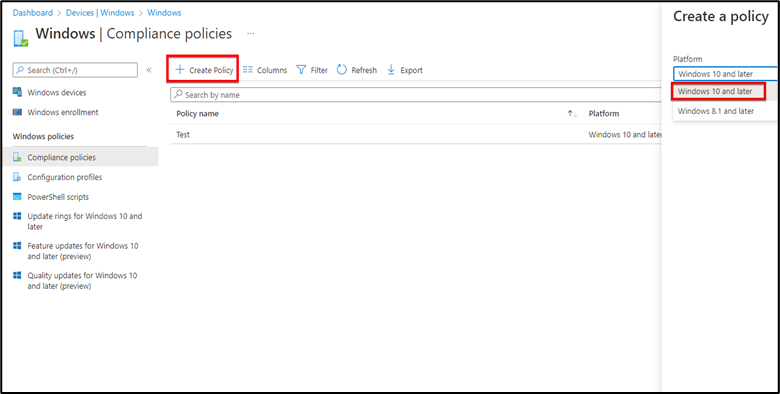
Step1 : Open Intune portal go to Devices>Windows>Compliance Policies and create a new policy for your Windows device.
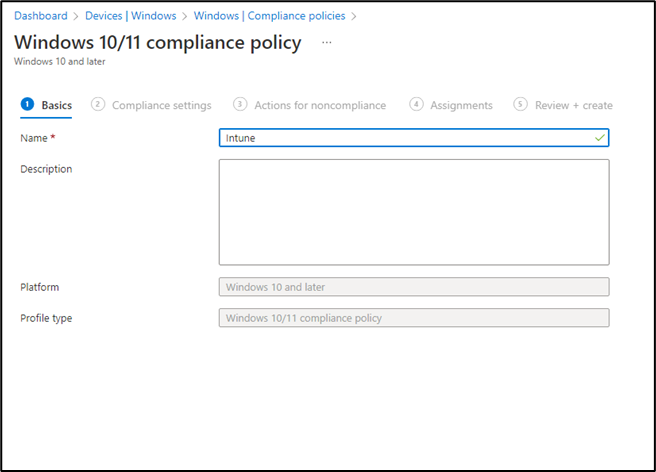
Step 2: Name the policy and hit next
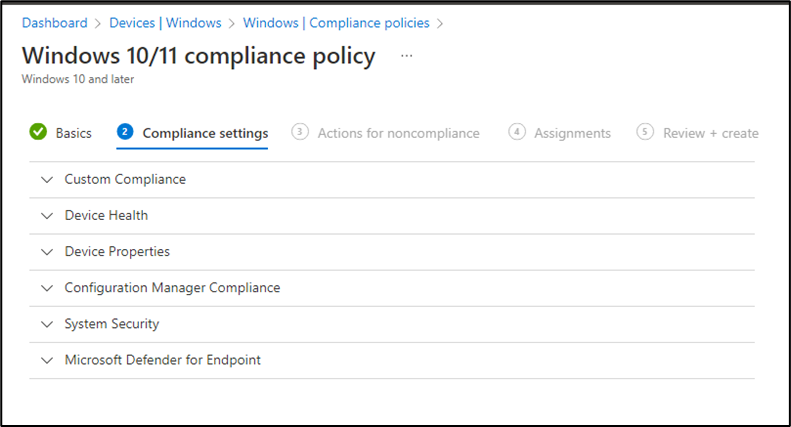
You will have 6 built-in settings in Compliance. These settings will help us to show that whether that device is compliant or noncompliant.
- Custom Compliane: In custom Template setting you can upload your organizational policy.
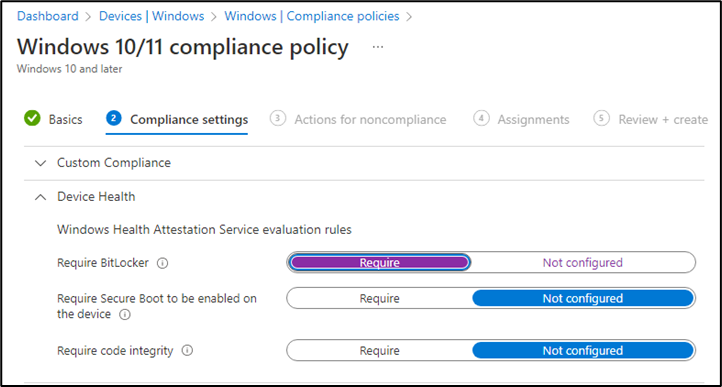
- Device Health: It has 3 security rules which I’ll show you later in the article.
- Device Properties: Where you define minimum or maximum OS version.
- Configuration Manager Compliance: This is if you have hybrid system with System Center Configuration Manager.
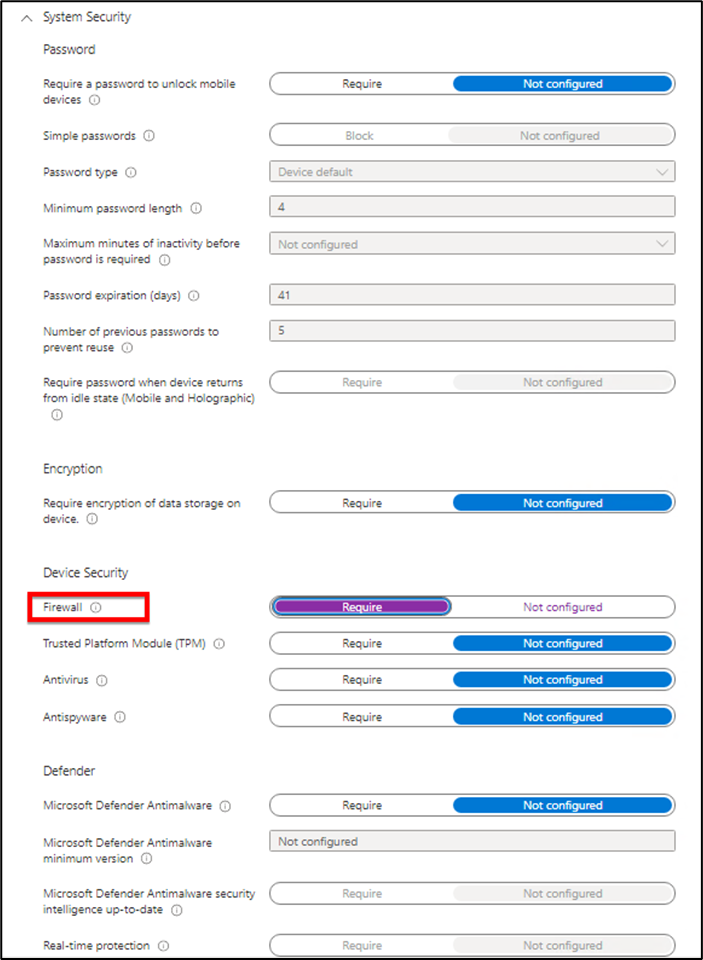
- System Security: This is where you can define Password policies and other security options like Antivirus, Firewall etc.
- Microsoft Defender for Endpoint: We use this policy if we have O365 Defender “Advance Threat Protection” in our Environment.
Step 3: I will leave the Custom Template settings and will move to the second setting “Device Health”. In that setting we will have 3 options and you can enable the required one. I will enable Bit locker option only. Require secure boot option if you want to boot in the factory trusted state and Code Integrity if you’re looking into the integrity of the drivers and system files.
Step 4: You can set the password policy and it is same as GPO. If you have Hybrid Environment then configure it from your on-premises AD server. You can enable the options according to your requirement. After enabling the settings hit next.
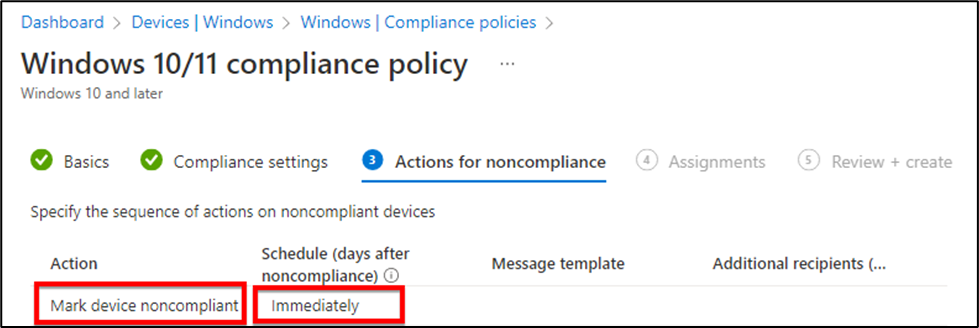
Step 5: In the next tab, you’ll have “Actions for noncompliance”, I selected mark device noncompliant and update us “immediately”.
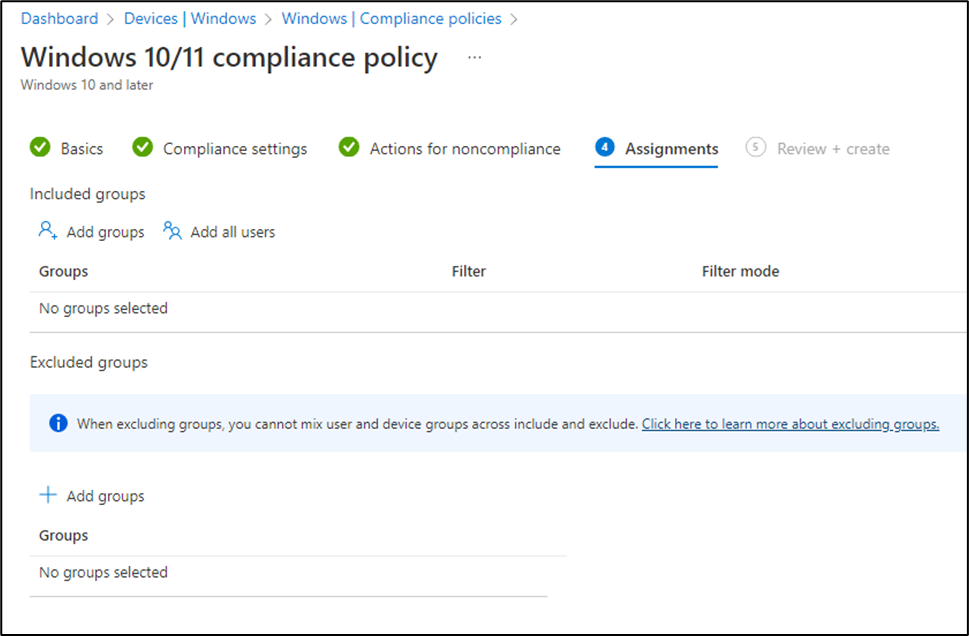
Step 6: Assign this to users or group then review and create. It will take affect in few minutes and then you can check the status of your device.
Step 7: To check the status go to the Devices> Windows > Compliance Policies and open your newly created profile. Select the device then from left side select Device Status> Device Compliance.
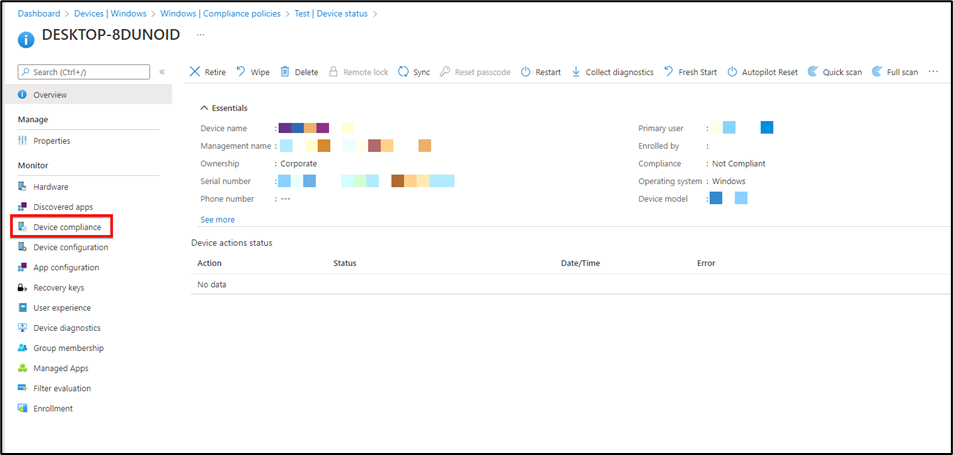
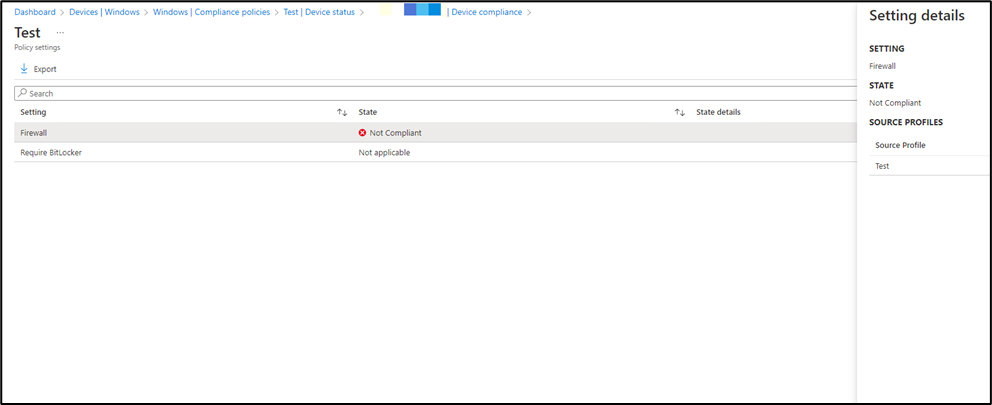
Here you’ll see if the device is compliant or noncompliant. I turned off my Firewall and didn’t enable bitlocker to check. It gives the correct results, you can see below.
Let me know if you found this article helpful.