Passwords were only managed via Default Domain Policy before server 2008, so ONLY ONE password policy was possible across the domain.
In Server 2008 and onward Microsoft introduced Fine-Grained Password Policy and you can manage multiple passwords polices by PSO (Password Setting Objects)
Deploy Fine-Grained Password Policy
Mock-up Presentation
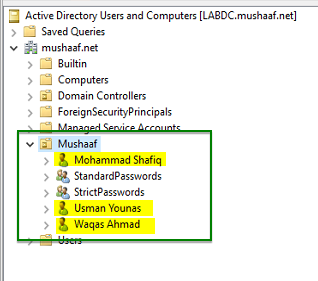
Here I have created 3 users in my AD
- Mohamad Shafiq that belongs to no group
- Waqas Ahmad that belongs to StandardPasswords group
- Usman Younas that belongs to StandardPasswords and StrictPasswords groups.
Password Settings Object creation
First open ADAC (Active Directory Administrative Center)
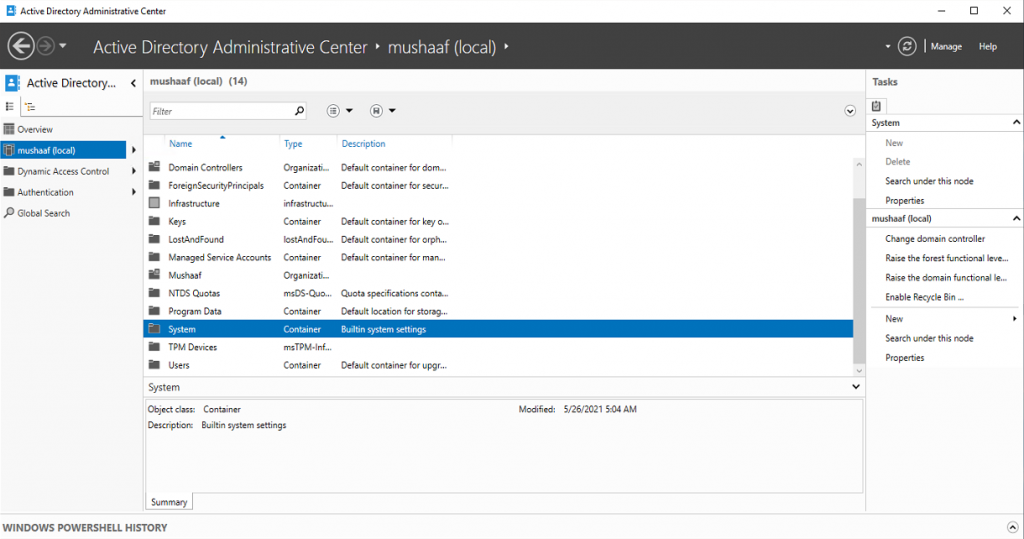
Click on your domain (our is called mushaaf.net) to list containers in your domain. Click System Container.
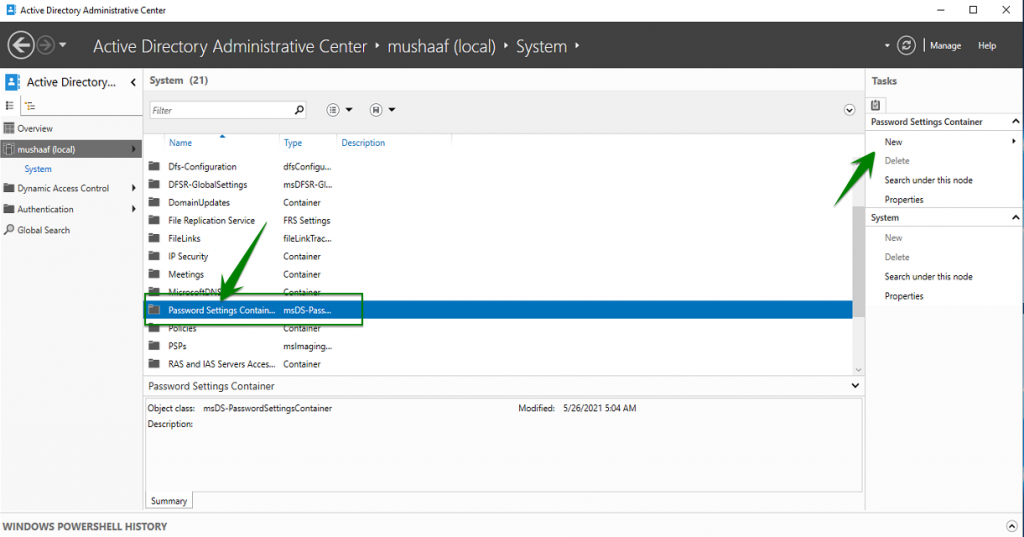
On the PSO creation screen, you can see the password policy parameter such as password length, password history, maximum age, complexity etc. There is also the Precedence parameter. As you can see on below screenshot, I have applied PSO to StandardPasswords group. For these examples, I have removed the minimum password age to validate just after account creation my PSO. If I leave this setting to 1 day, I have to wait tomorrow to change password …
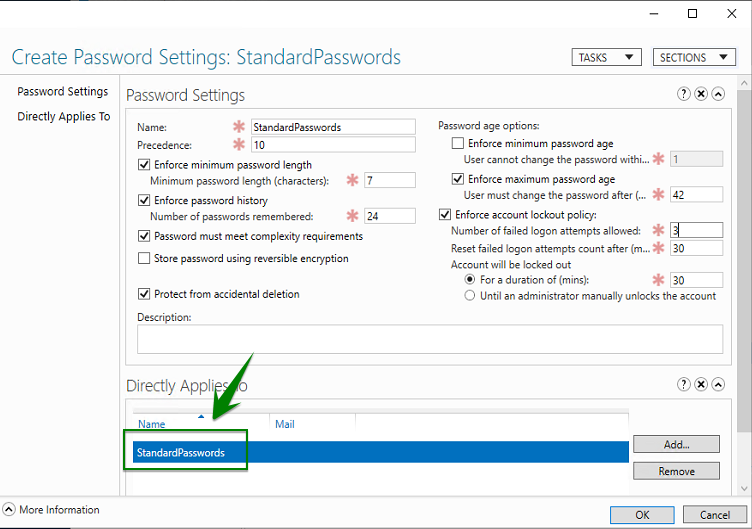
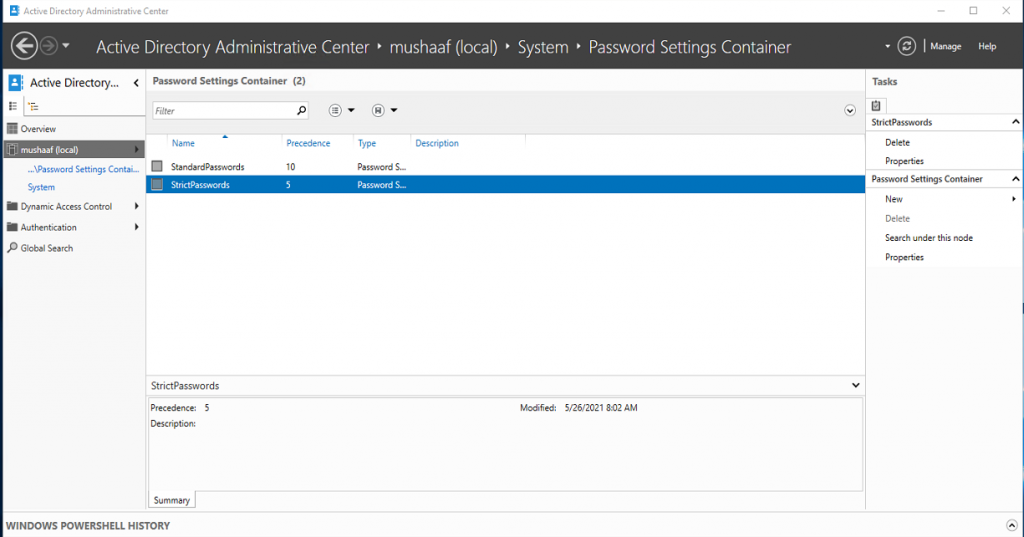
After PSO creation you can double click on the Password Settings Container to view your PSO. On the below screenshot, you can see that my StrictPasswords PSO has a stronger precedence.
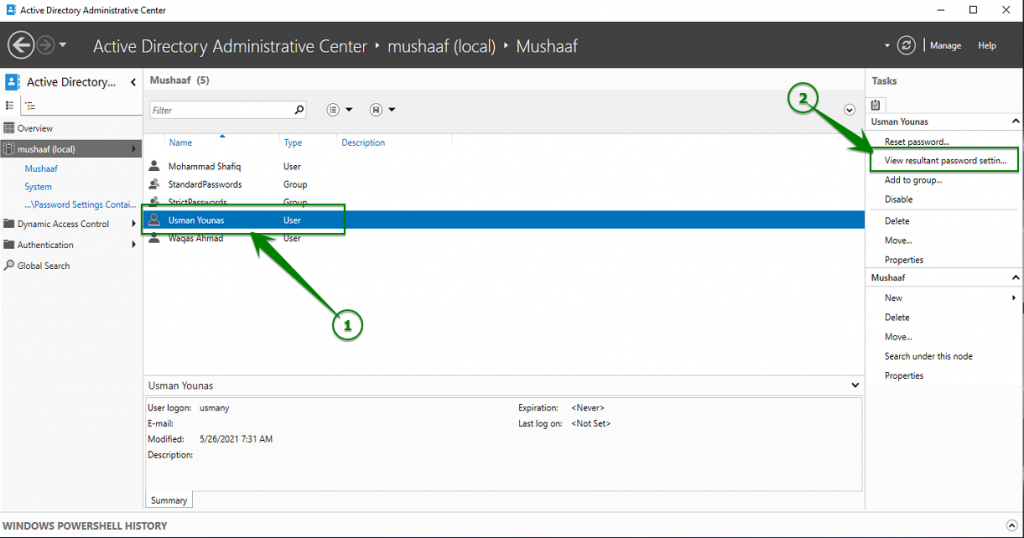
To view the RSOP and so the PSO that will be applied to users, open your OU where are stored your users object and select an account as below. Click on View Resultant Password Settings on right.
Remove default password policy on Active Directory
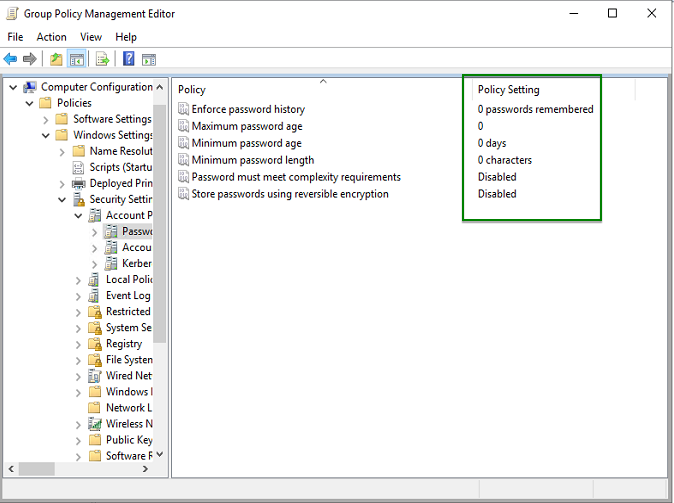
To validate our test, I have to remove the default password policy managed by the Default Domain Policy GPO. Open Group Policy management console, and edit the Default Domain Policy.
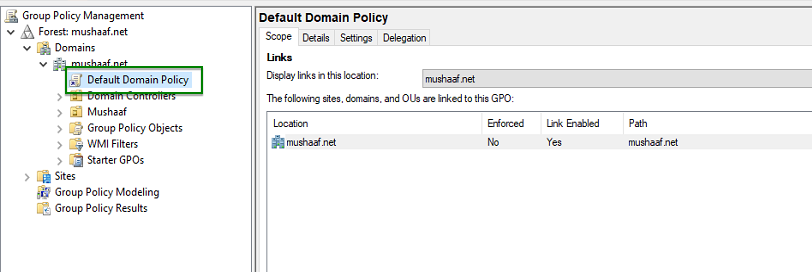
Open Software Settings, Windows Settings, Security Settings, Account Policies and Password Policies. Set these policies as below.
First test: user without password policy
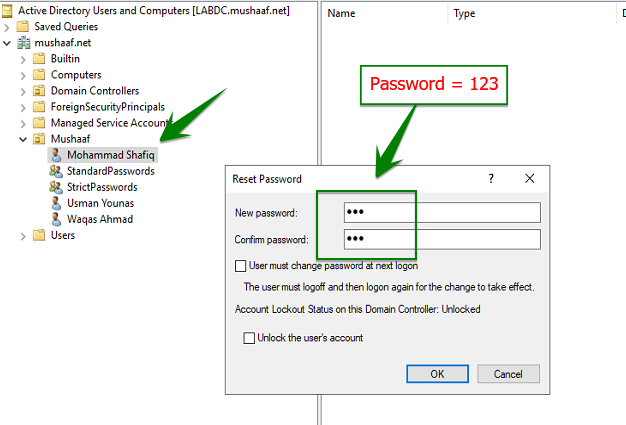
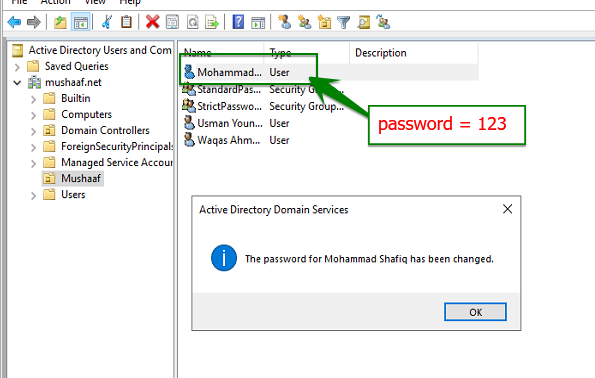
My First user called Mohammad Shafiq belong no group. So no password policy is applied to this account. To test that, I change the password to ‘123’ as below:
Second test: User with StandardPasswords PSO
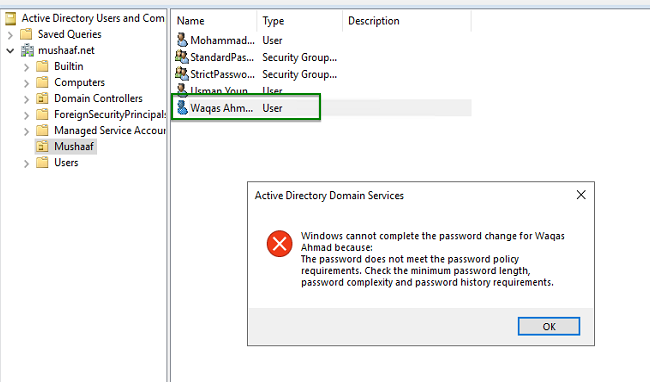
The user Waqas Ahmad is linked to the StandardPasswords PSO. A 8 chars complex password is required. So I try the 123 password:
So I try a complex password more than 8 chars and then its SUCCESSFUL!
Third test: User with StrictPasswords PSO
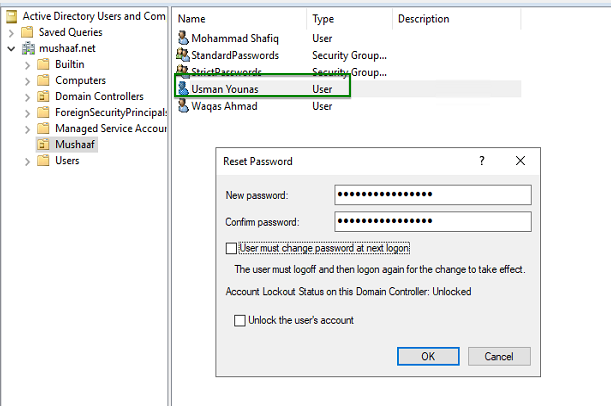
Now I will try Usman Younas user. This user is a member of all my PSO group. But because StrictPasswords PSO has the strongest precedence, this is this last that will be applied. Let’s try to validate this assumption. I tried password “Welcome1” and got the same error as above because this password doesn’t meet the StrictPasswords PSO requirements.
So I generate a strong password with this online tool https://passwordsgenerator.net/
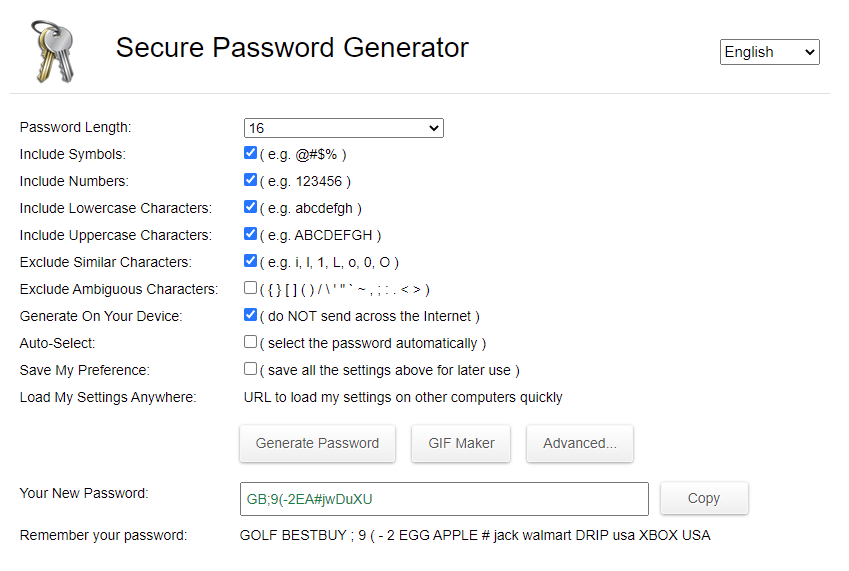
Next I will Paste it to the reset password wizard:
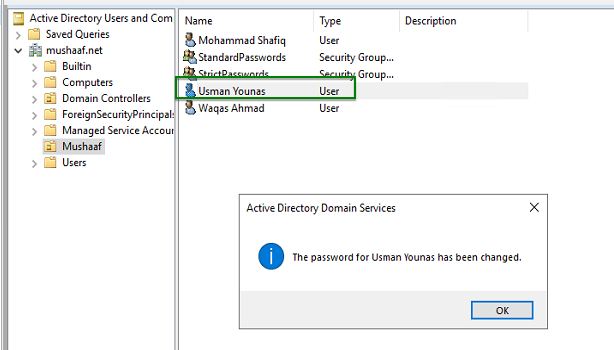
And it is work !
Conclusion
Fine-Grained Password Policy is a great feature that enables to apply different password policies in your domain. For example you can apply a different password policy to administrator, to standard user and to service account. You are no longer forced to use only one password policy. Now that Microsoft has introduced the Active Directory Administrative Console (ADAC), Password Settings Object can be managed easily!



