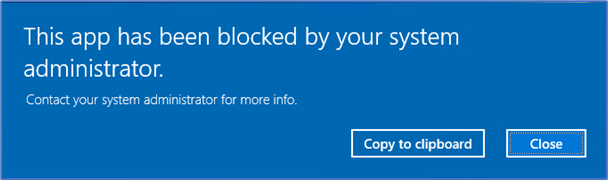
Recently, we had a requirement to restrict specific applications for a certain group of people due to license limitations and client had only purchased minimum licenses they required. Client is using RDS “Remote Desktop Server” and don’t want to allow everyone to use application and break their licensing.
There are various articles and documentation pointing to deny application/s to certain users, however this requirement was in other direction as to allow only specific users.
Below article is a step-by-step article to utilize App Locker feature in Windows Group Policies and restrict, also keep in mind that this feature is not applicable on Windows 10 Pro SKU so you must be running Windows 10/11 Enterprise Edition. In our case, we had Windows Server as terminal server so didn’t had that issue
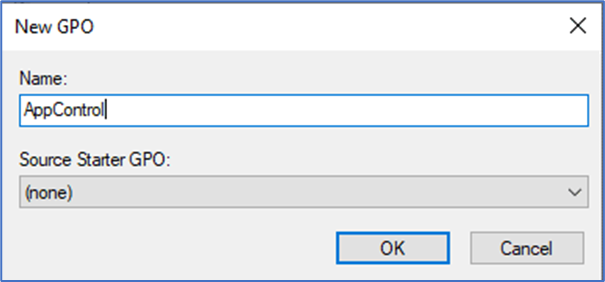
- Go to Group Policies Objects and Create a new policy AppControl or name it as you want.
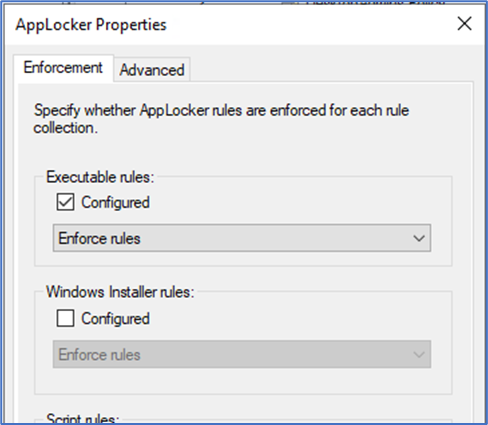
2. Go to “Computer Configuration > Policies > Windows Settings > Security Settings > AppLocker > Right Click and Select Properties
Set Executable rules as “Enforce rules”. You can also select “Audit Only” which is good method if you are new to this and looking to test the feature. You will see Event Logs mentioning the audit logs and can make sure that you are not blocking anything legitimate.
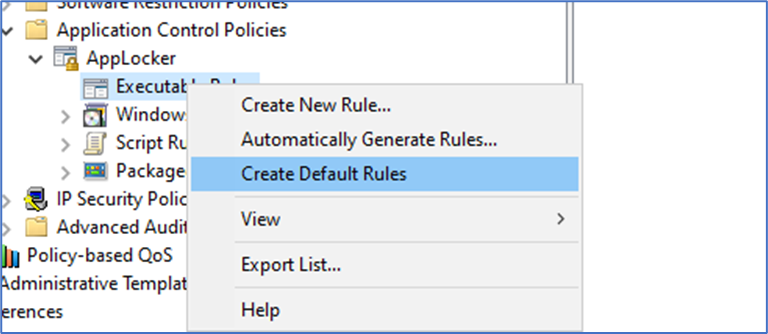
3. Next, Click at “Executable Rules” and Select “Create Default Rules…”. This is to create a default rules so you allow all your required applications for ProgramFiles, ProgramFiles<x86>, Windows Folder etc.
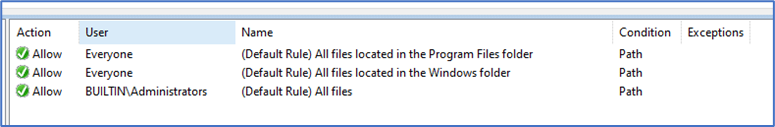
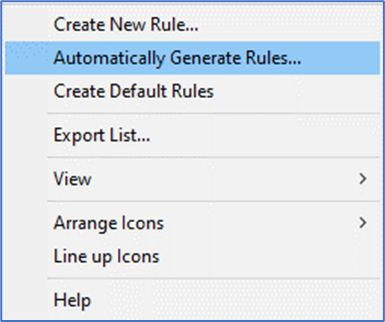
4. You can also Automatically Generate Rules by defining your path. It is good idea to define all the path and generate rules based on installed applications.
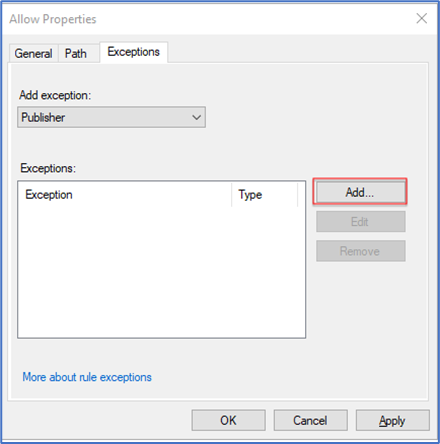
5. Now go to one of the default/existing rule matching your installed application path and create exception for the application/s that you want to restrict.
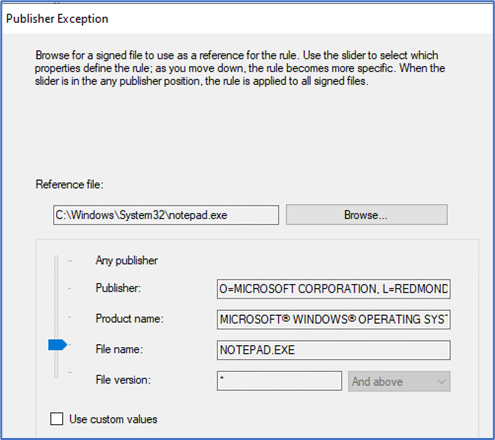
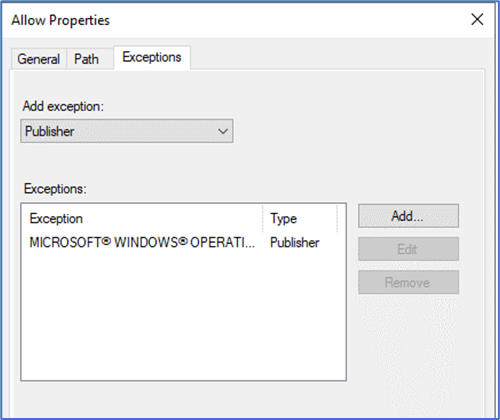
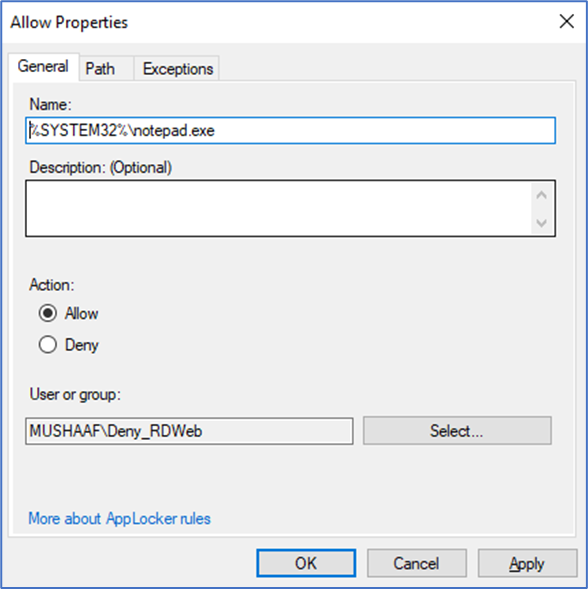
6. Now create another rule, specify the group/user that you want to allow and select the application using file path, hash etc.
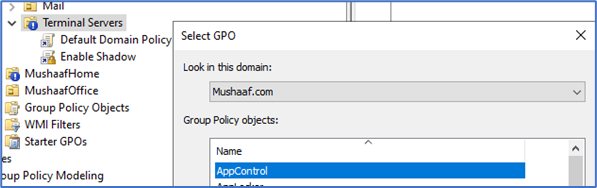
7. Allright, hardwork is done and the next part is to link this GPO to an Organization Unit where you RDS Server/Computer exist.
8. Wait for the Group Policy update or run “gpupdate /force” on the destination Server/Computer. Now other users except mentioned will see a deny message when launching that application.